What’s the Best Practice in Using NTFS Permissions and Share Permissions?
What is the best practice in combining NTFS Permissions and Share Permissions?
This is a common question asked by most users, even Administrators.
Read here for an answer!
In this blog post, we’ll talk about the best practice in combining NTFS Permissions and Share Permissions.
In fact, searching for this topic online yields quite a handful of results. You would also notice that some people have their own “best practices” as opposed to what Microsoft advocates for.
I believe the confusion stems from the differences in how Share Permissions were done in the past and the changes made in the modern operating systems.
For example, the Guest account is automatically enabled in older OS, and it is part of the “Everyone” group. This creates a problem because whatever access is given to “Everyone”, Guests inherits it.
This is why even today’s Administrators are still using Authenticated Users group to separate Guest and non-Guest users. Fortunately, this has changed in the modern OS.
So, are you ready to know the best approach?
Here we go!
Give “Everyone” Full Control on the Share permission and define specific permissions on the NTFS level
To better understand this, let’s have a quick comparison between Share Permissions and NTFS Permissions.
Simply, a Share permission is what you set to a folder when you share it. The Share permissions determine the type of access others have to the shared folder across the network.
You can view the Share permissions by going to the Folder properties, clicking on the Sharing tab, Advanced Sharing, and finally Permissions.
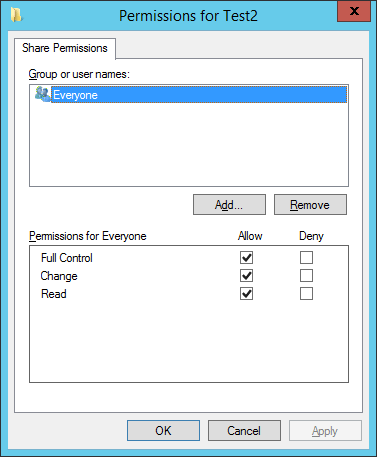
The NTFS permission, on the other hand, determines who can access a file or folder and what level of access can be made to the resources, both across the network and locally.
You can view the NTFS permissions by going to the Folder properties and clicking on the Security tab
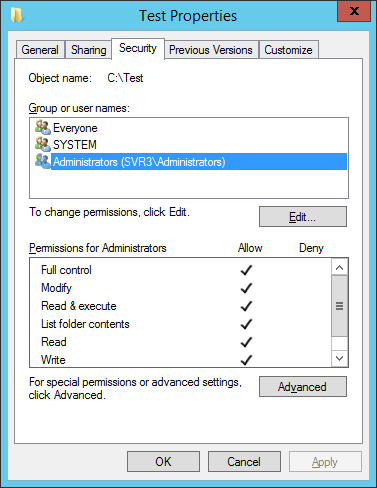
The most restrictive wins!
When there is a conflict between Share and NTFS permissions, the most restrictive permission applies.
Whichever of the two is more restrictive is applied as the effective permission – what the user can actually do to the files and folder.
To illustrate this, suppose a user has a Share Permission – Read and NTFS Permission – Full Control. Applying what we’ve learned, we can conclude that the effective permission given to the user is only Read.
Similarly, if that order is reversed, and we have Share Permission – Full Control and NTFS Permission – Read, does that change the effective permission?
Absolutely not! Again, the most restrictive permission applies.
Wrapping up!
NTFS and Share permissions can be likened to a security system used in a large company.
Let’s say we have a lobby where everyone can enter. From the lobby, there are doors that lead to Operations, HR, and the IT rooms.
Each employee is given a badge and a proximity card that they can swipe to authorize access. IT people can use their card to enter the Operations area and the IT Room.
HR people have access to HR and Operations rooms. Someone from the Operations department is only given access to the Operations room.
You see the point here?
The access to the lobby is the Share permission and the access programmed on each card that opens specific doors is the NTFS permission.
I hope these clear things up.
To learn more about NTFS Permissions, Share Permissions, and how to use them, get your free course HERE!
Prevent Unauthorized Access to Sensitive Windows Folders!
Get your free trial of the easiest and fastest NTFS Permission Reporter now!




I always did just like that. But on my current organization it doesn’t work as expected.
Windows Server 2008 R2 SP1 all patched up.
I’ve set the share permissions to “Full control” and the NTFS permission of some group to “Write”. The users of that group shouldn’t have the ability to set permissions on files and folders right? But that happens…
My solution to that environment was to change the share permissions to “Change”, and now they aren’t able to set permissions on the files and folders.
Funny we just discovered the samething here… Microsoft told us that it’s new since Win2008 and when a user create a folder/file he his the owner and can change the permission….