Take Ownership of Windows Folder and Files
What you need to know before taking Ownership of Files and Folders
Taking ownership of files and folder is an easy thing to do. Instructions are all over the internet that even a regular Windows user will find it simple and effortless. But have you ever wonder why you need to do this and it’s effects? Now before you take the ownership of all folders in your PC (please don’t!), I will share some information about taking ownership of files and folders.
Concept of File and Folder Ownership
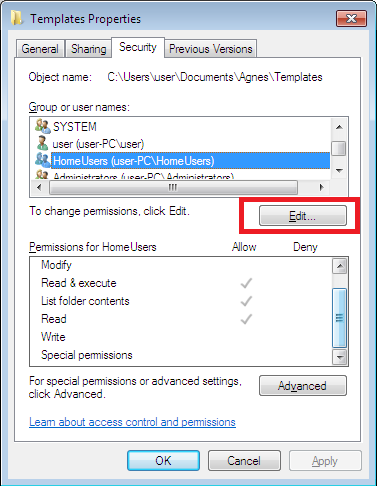
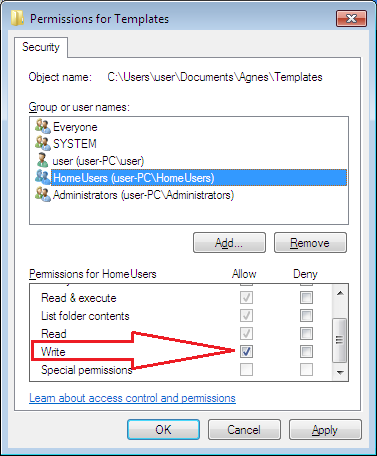
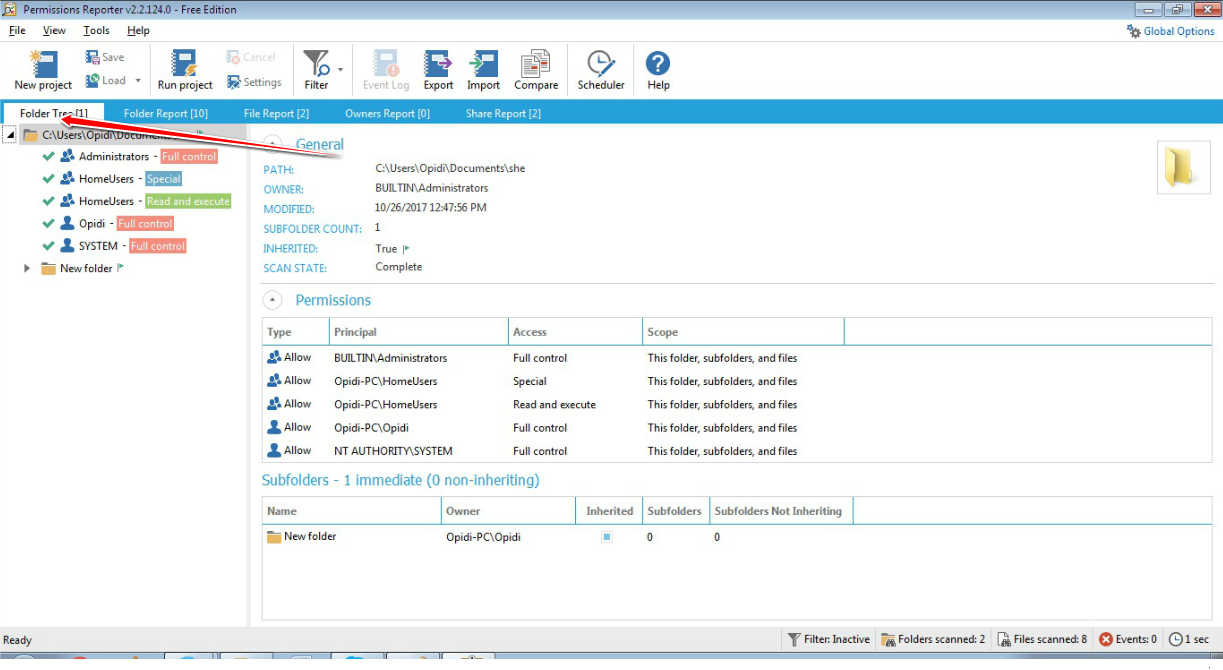
The owner controls how permissions are set and to whom permissions are granted on the files and folder. By default, the owner would be the user who created the object. In simple terms, if you created a folder then by default you become the owner of that folder and having ownership means you get to decide who can access the folder and gives you the power to transfer the ownership to another user.
Who can take and transfer ownership
As mentioned above, the default owner, the user who created the file or folder can transfer the ownership. But aside from the owner, other user or group with certain permission can also take the ownership. These are:
- Member of the Administrators group
- A user with taking Ownership permission
- Member of the Backup Operators group
Why do you need to take the ownership?
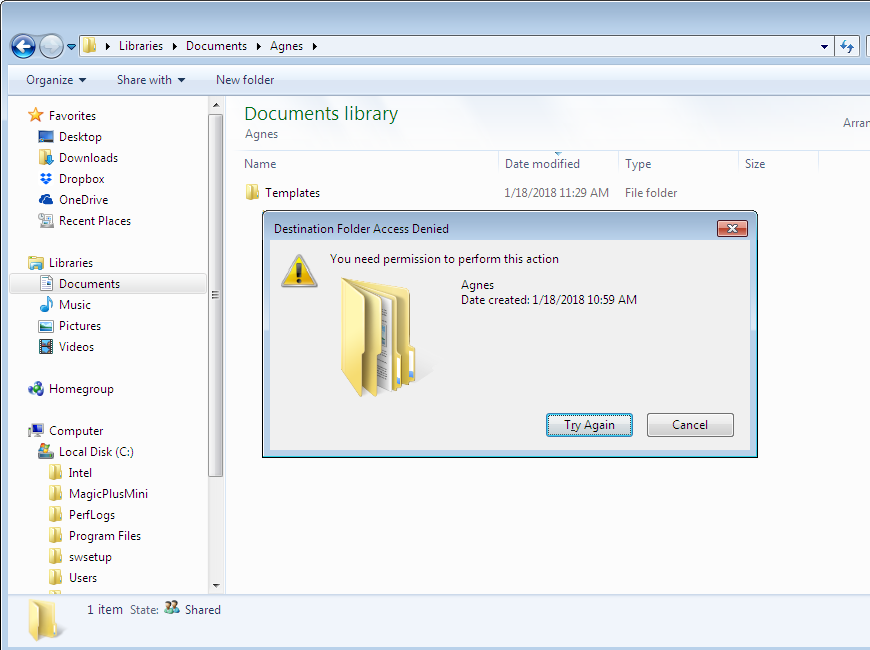
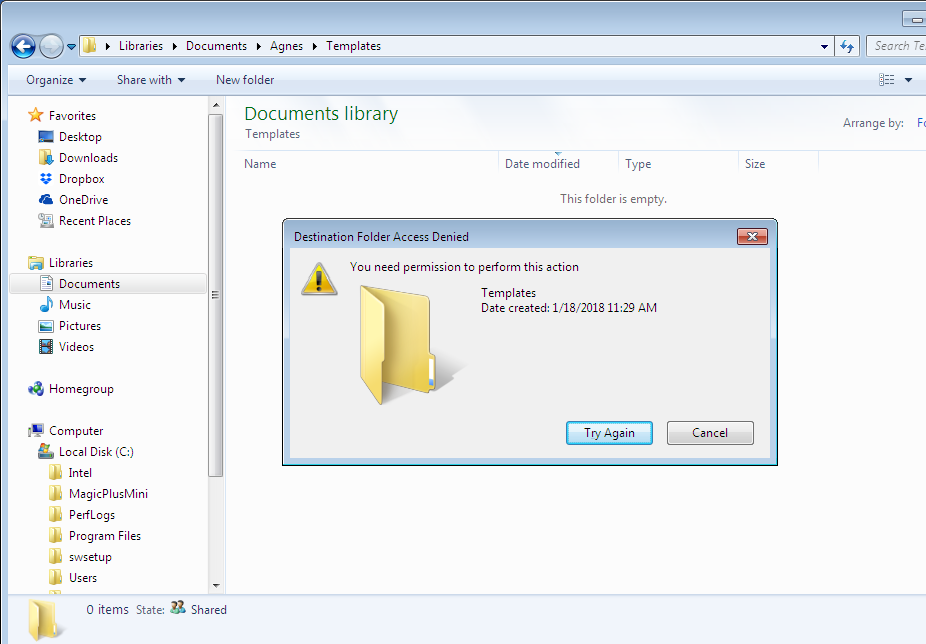
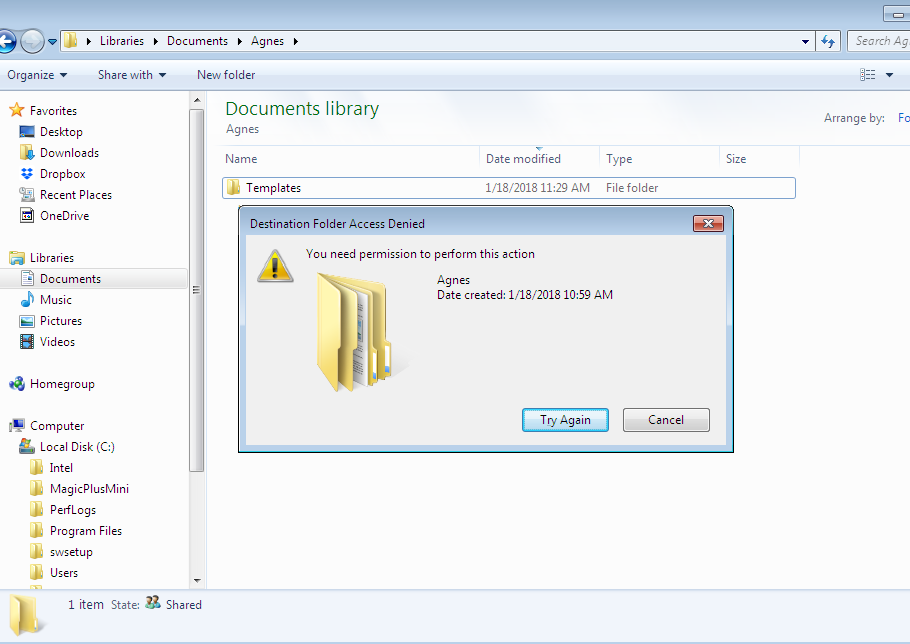
Because you can! Just kidding! Have you tried deleting or renaming a folder but you get access denied? That’s most likely caused by lack of permission, and being the owner of the folder allows you to do some changes on that folder. This is just an example why taking ownership is needed, and I’ve listed couple more examples below.
- You connect an external drive from another PC, and you’re denied access to the folders
- Upgraded from Windows 7 or 8 to Windows 10 and you wish to delete Windows.old folder to free up some space
- You attached the 2nd disk to your PC. The disk used to be a system drive (with OS Installed), and you’re denied access to the folders
- Make changes to system files (example: replace a bad .dll file)
- Manage files or folder owned by the user account that’s already deleted
How to take ownership of the files and folders?
Here I will show you how to do it via GUI. There is also a built-in command line tool in Windows called takeown.exe if you want to do it via command line.
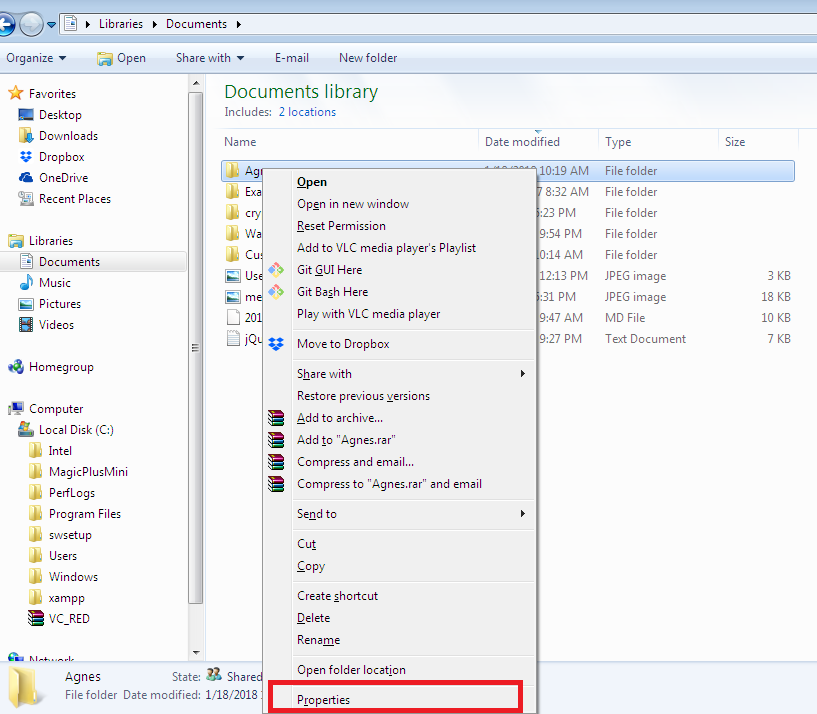
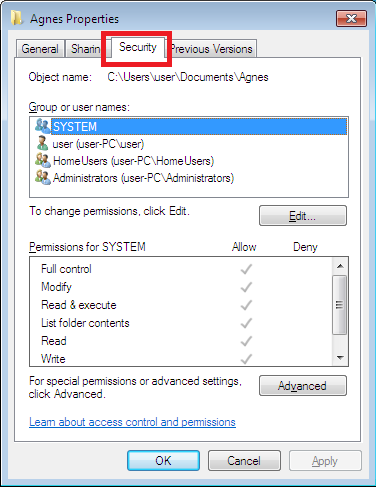
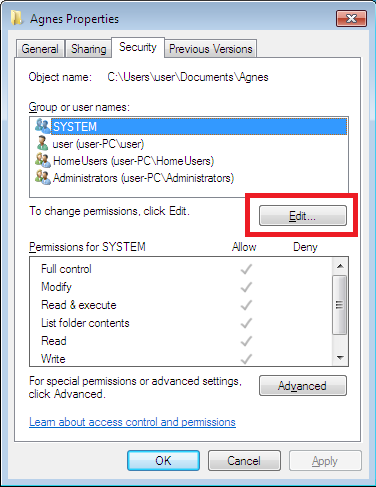
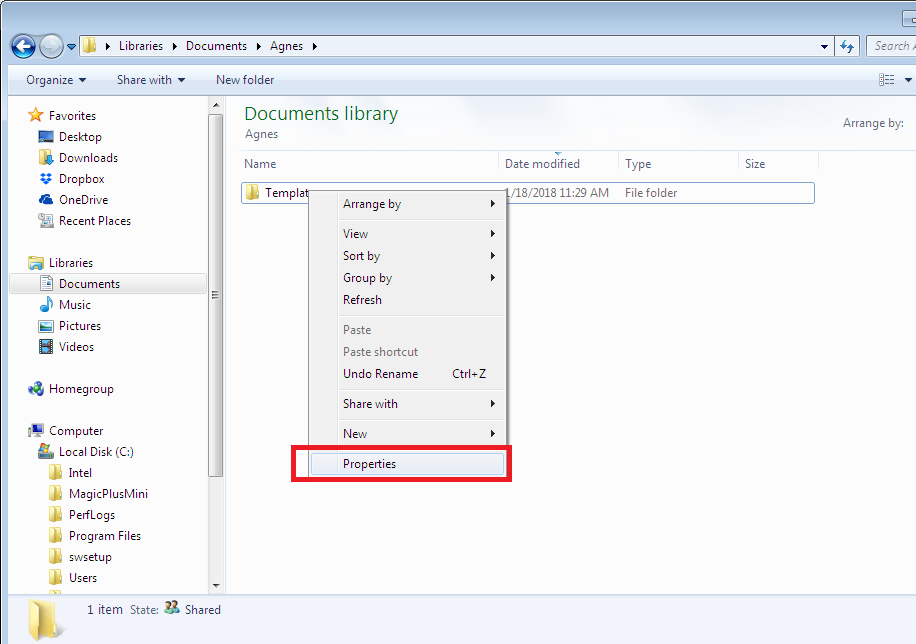
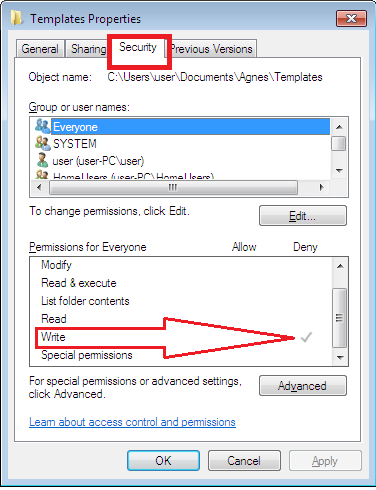
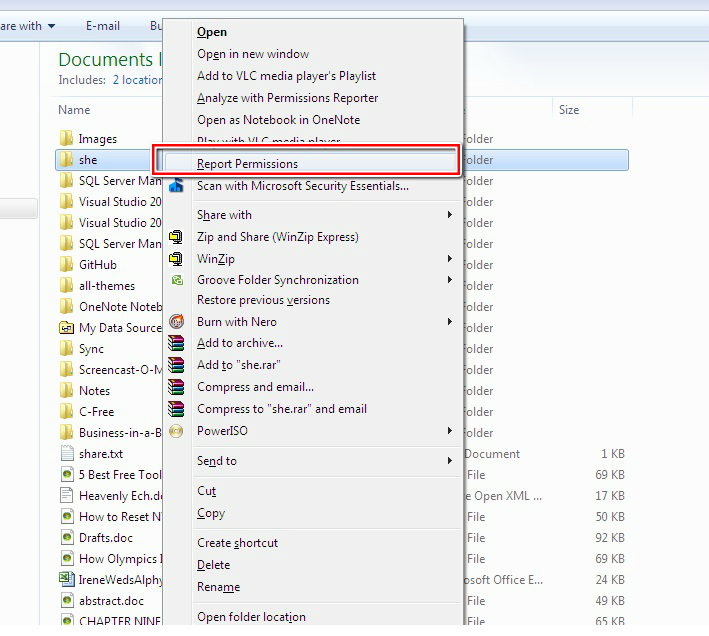
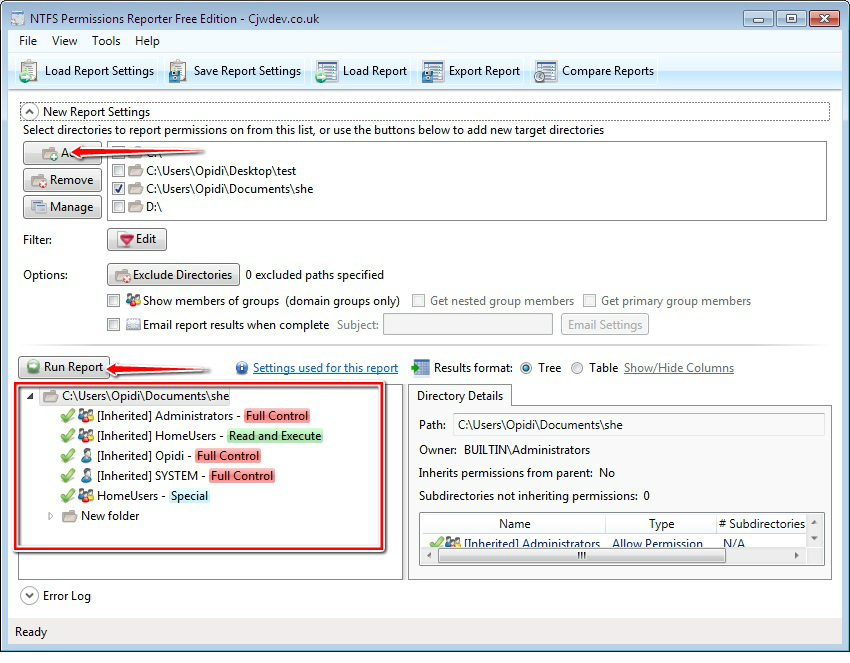
In this example, we will take ownership of the System32 folder. Right-click the folder you wish to take the ownership and go Properties. Click on Security tab and then Advanced
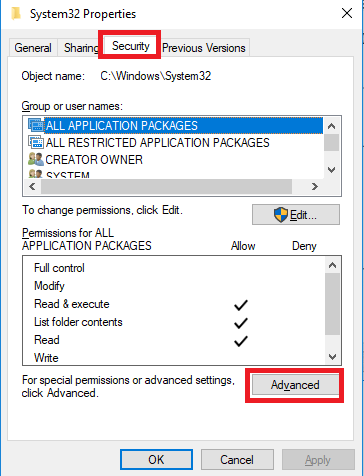
The Advance settings will show you the current owner of the file or folder. Click on Change

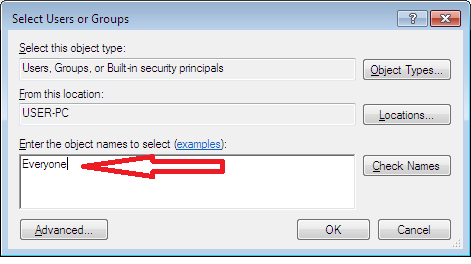
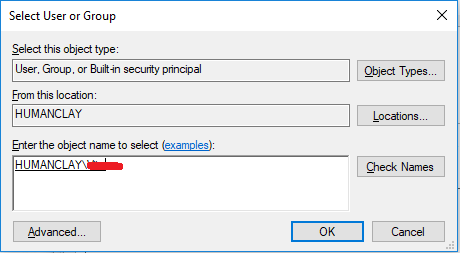
Enter the name of the new owner and click Check Names or click Advanced to find the user.
Once the new user is entered, click OK and now the new owner will be shown. Tick the option “Replace owner on subcontainers and objects” if you also want to take ownership of the subfolders and files. Click OK and you’re done!
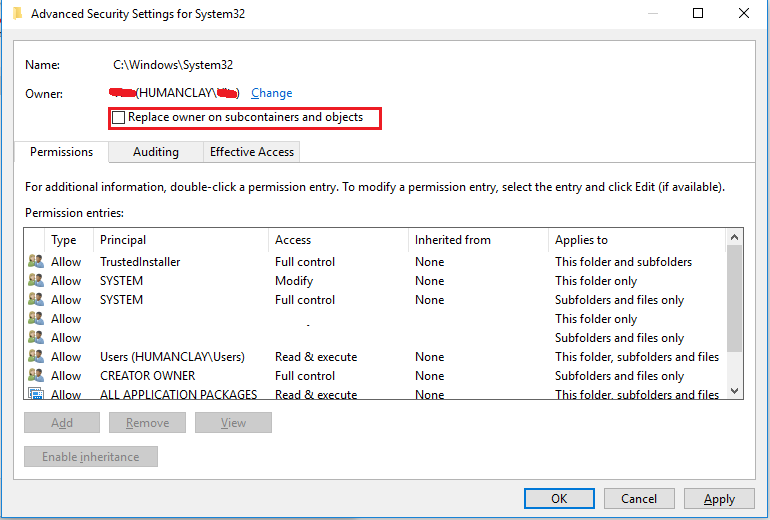
Taking Ownership from TrustedInstaller
Although this article talks about taking ownership of files and folders, it is critical to know that taking ownership from TrustedInstaller can lead to system failure. The TrustedInstaller account is used to secure core operating system files and registry keys so unless you’re very sure of what you’re doing then I don’t recommend messing with this.
Wrapping up!
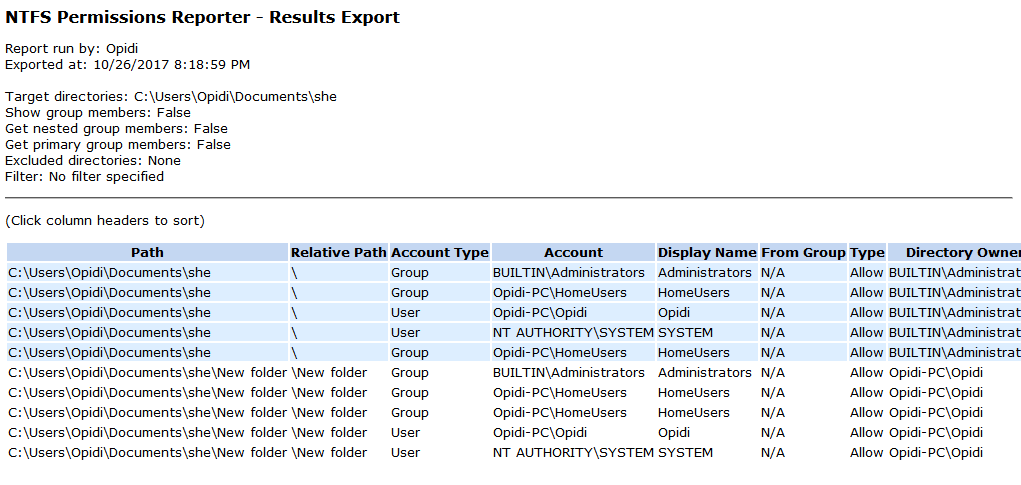
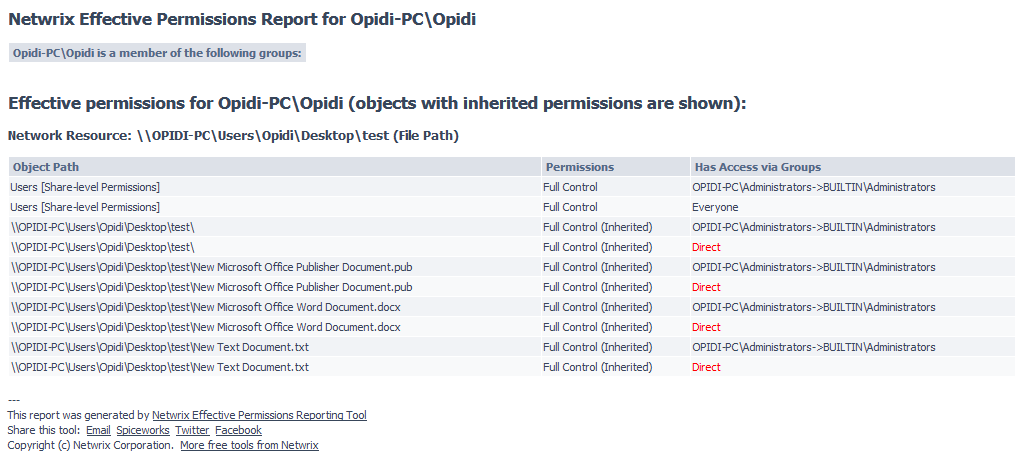
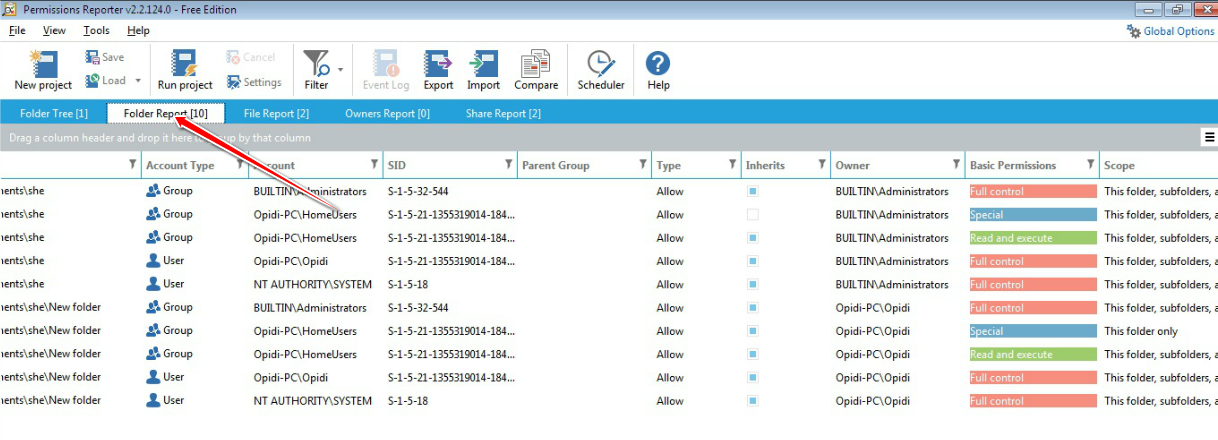
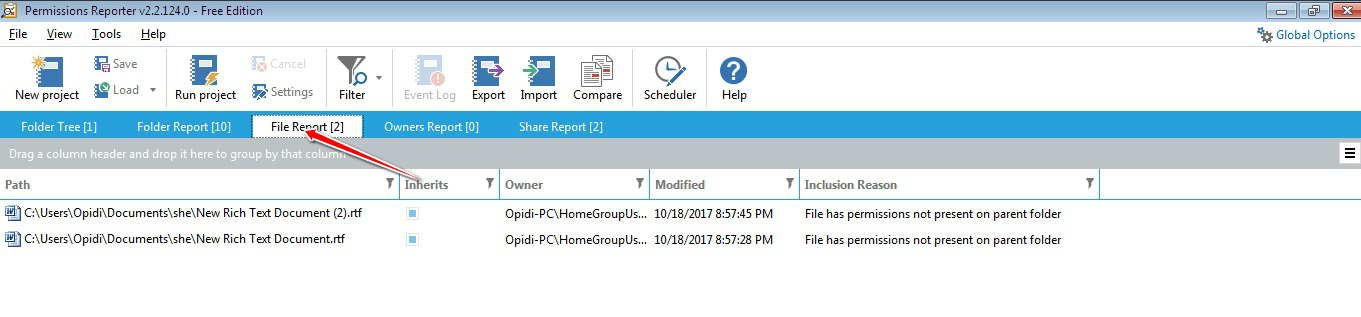
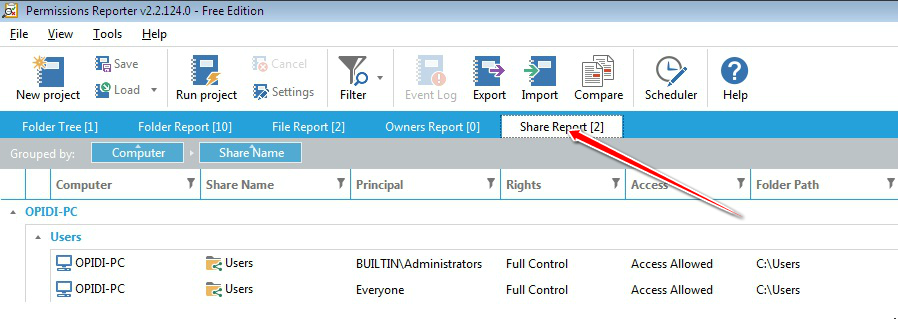
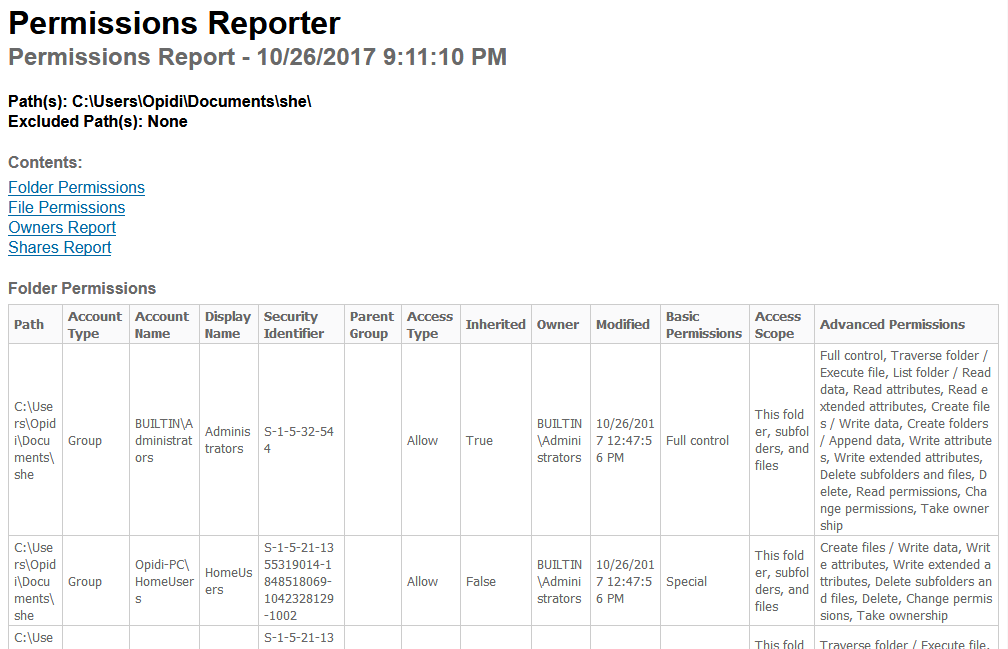
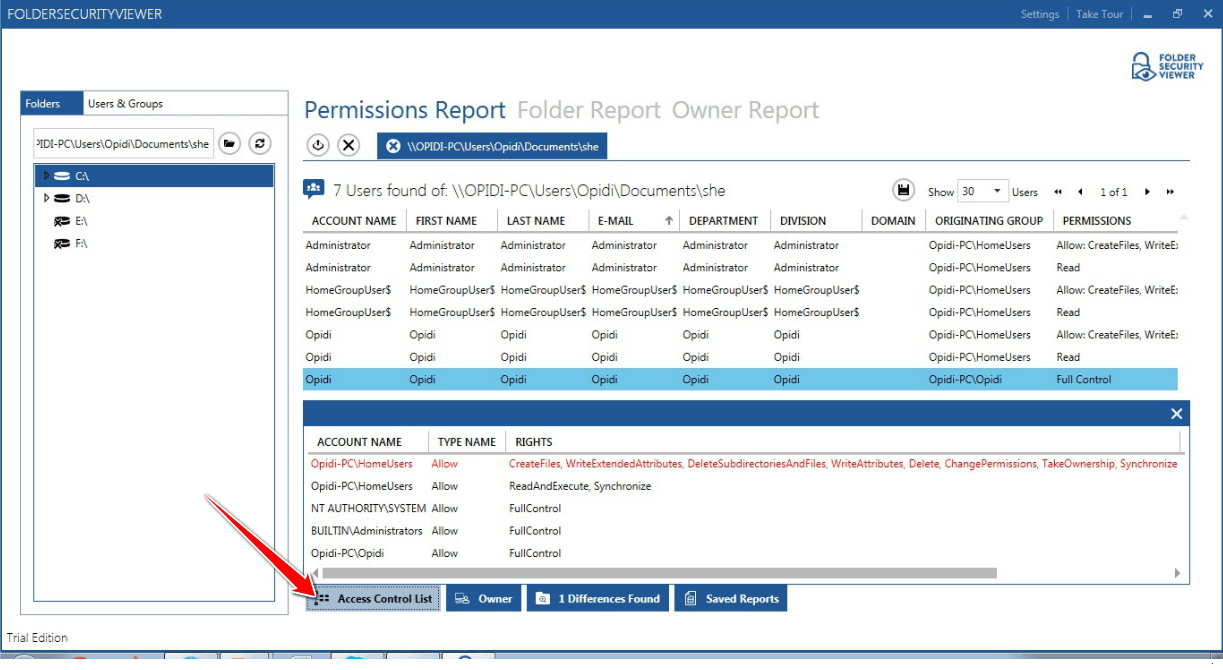
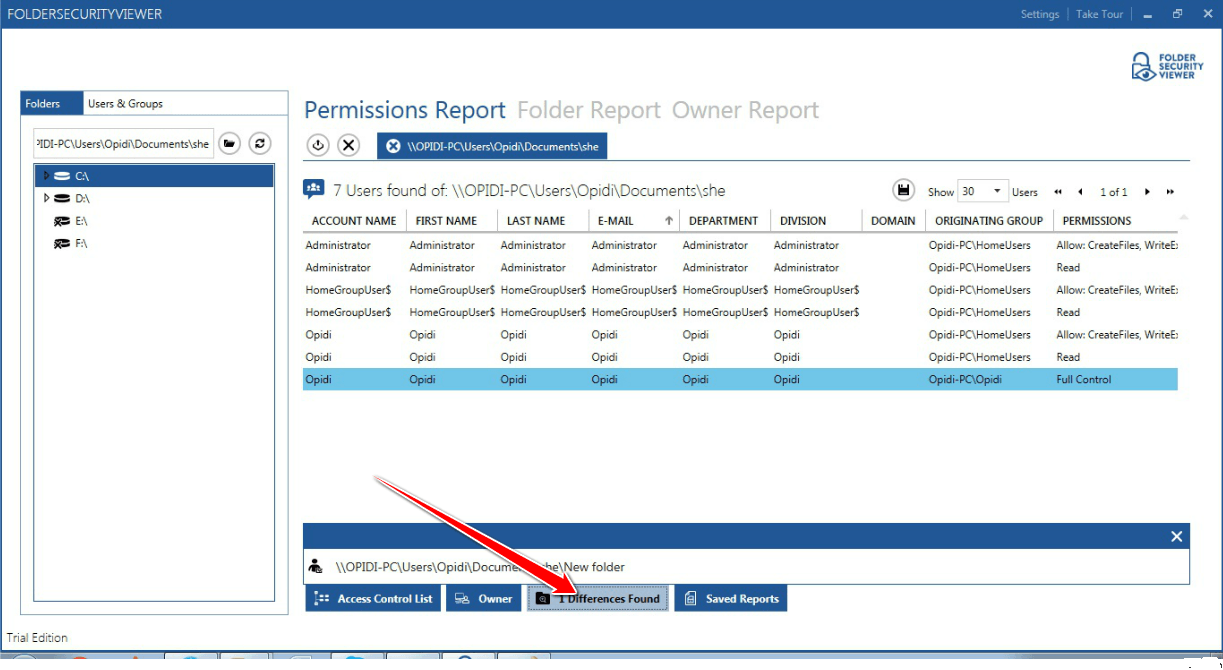
Taking ownership of files and folders will give user capability to override restrictions and allow them to perform the necessary task. However, always take extra precaution when changing the ownership especially on system files. Have I said that already? Well, that’s because I wanted to emphasize this. If you need to change it for temporary access then, by all means, do it but don’t forget to change it back to the original owner (TrustedInstaller) to avoid issues with the Operating System. You might also want to keep track of which folder a user own as some users may have taken ownership of certain folders. If you’re the only user or admin on your PC, then it might not be necessary but for a larger organization, having a tool like FolderSecurityViewer will help you with this task. Be sure to check it out!
Useful Resources
- https://blog.foldersecurityviewer.com/how-to-reset-ntfs-file-permissions/
- Our NTFS Course is a good resource to start learning about it: https://www.foldersecurityviewer.com/ntfs-course