How To Hide All NTFS Alternate Data Streams
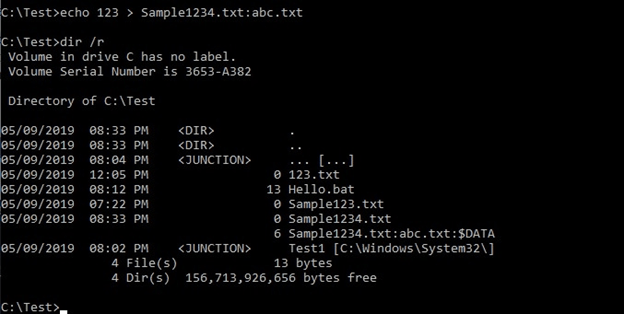
It’s possible to dump Alternate Data Streams (ADS) using the /r switch in the dir command.
Moreover, you can also use the streams.exe tool found within the Windows Sysinternals to dump the streams
On earlier Windows versions, ADS was hidden by concealing the reserved names as the base names.
Examples of such names include CON, NUL, COM1, COM2, LPT1, and others.
However, in Windows 10, this seems to be fixed; and doing the same may not be possible, but it still works.
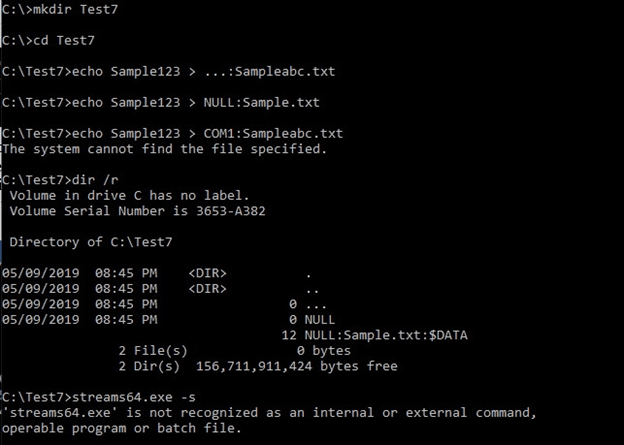
The ADS on “…” was successfully created and listed by the tools.
Creating an ADS on COM1 results in an error, but does not have an effect on the system.
ADS can also be created on the drive using echo Sample123 > C:\:Sampleabc.txt that hides it from the dir/r command inside the C:\.
However, it will show the ADS inside subfolders of C:\ for the “..” directory, as shown below
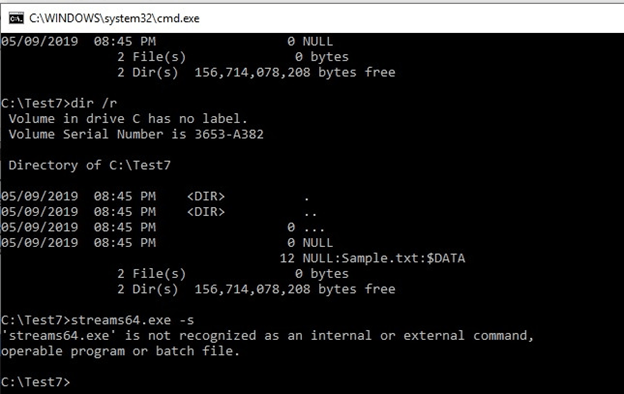
The 12 NULL:Sample.txt:$DATA was created by the C:\:Sampleabc.txt ADS. This stream is also visible using the Sysinternals streams.exe tool, if it is called on directory C:\. You can use the “…” to hide it from both tools.
There is also another way of hiding it by using “<space>”at the end of the file, and Windows will automatically remove the space.
However, we can create such a file with ADS using tools that cannot open the file because of the file name. After truncation, it will be changed to a name without any space, which, in actual sense, does not exist.
Have a look at the screenshot below.
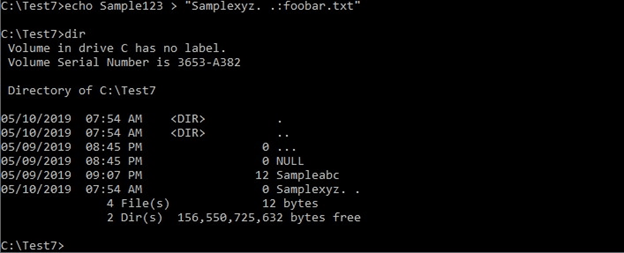
The ADS foobar.txt is not visible using the normal searching tools
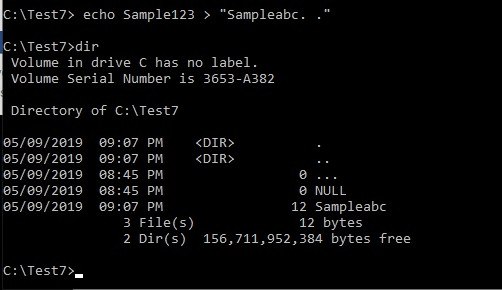
NOTE: such files can be created using the echo test> . ..:$DATA
Also, note that Sampleabc.txt uses the same ADS that was used to create one on C:\:Sampleabc.txt.
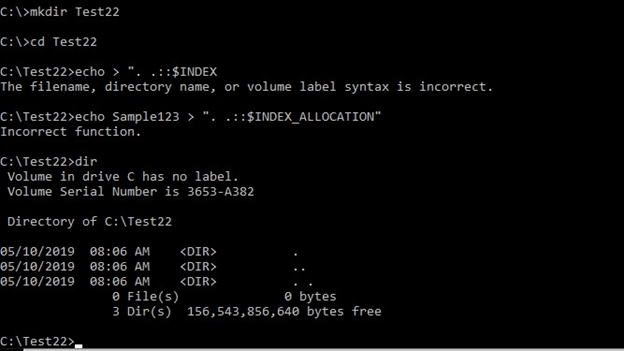
Going by that reasoning, we can create a directory with the name “..”, as shown below.
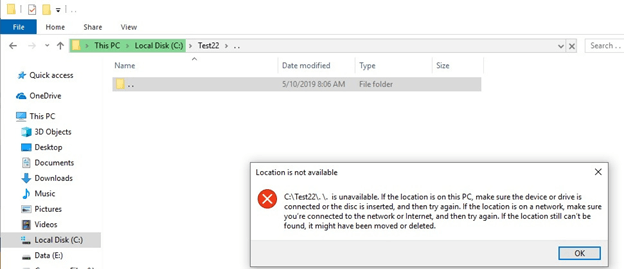
If you try entering the folder or opening it, you’ll get the following error.
Other techniques such as cd ..\..\ also do not work. However, cd “..::$INDEX_ALLOCATION” works (the double quotes are part of the command).
Directories using the name “..” can be entered using the earlier mentioned technique.
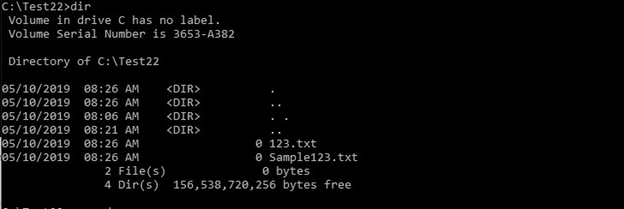
NOTE 1: The folder named Test22 can be opened through the GUI by clicking it twice and all its contents will be displayed correctly. The only downside is that you cannot open its files because Windows will interpret it as a wrong path. Using PowerShell will lead to endless loops when searching such folders.
NOTE 2: An ADS can be created on a folder with names such as Sampleabc, and be renamed by including a number, because the name will not work. To access the folder, you must rename it to its original Sampleabc name.
File System Tricks vs. Antivirus Products and Forensic Software
We conducted a quick verification of the file system tricks against an antivirus software to see if some malware could go past the system vulnerabilities. The most notable discovery was that files or folders ending with “..” bypassed the system with ease.
Upon re-enabling the antivirus software and scanning the folder and file, the program identified its own files, the folder containing the copied files, and bypassed the virus in “Sample123..” or in any of the “foo..” folders.
When the folder and the file were opened, the antivirus program found them because the contents were loaded from the system to memory. Using the “remove” action from Windows Defender could not remove the files but the “remove” action from the antivirus software deleted them.
You can change this behavior in the file guard settings by setting the scan to “Thorough” so that it can scan through all the files. The Windows defender blocks the reading of some antivirus’ text files.
Furthermore, we conducted another test using forensic software (in this case Autopsy 4.6.0) by loading “logical files” into the tool within the running system, and not using an image. As a result, we could open the “..” folder but not the “foo. .” folder.
If we created another file called “Valid”, in addition to the “..” folder that contained a space at the end of its name, it was read by the system as “..” and could be opened by double clicking.
This is possible only on “logical files” mode, disk image mode, and when running Autopsy live mode (with everything configured correctly to access data using the API).
Protect yourself and discover all permissions owner on your Windows fileservers!
Pass your next security audit without worrying about security leaks!
Get your free trial of the easiest and fastest NTFS Permission Reporter now!




Leave a Reply
Want to join the discussion?Feel free to contribute!