How to Hide the Binary Process in Windows
The Windows operating system automatically removes “..”at the end of each file. So, what happens if we have a process that uses the name “file1..” to check the signature of Antivirus products?
We can try to see what happens:
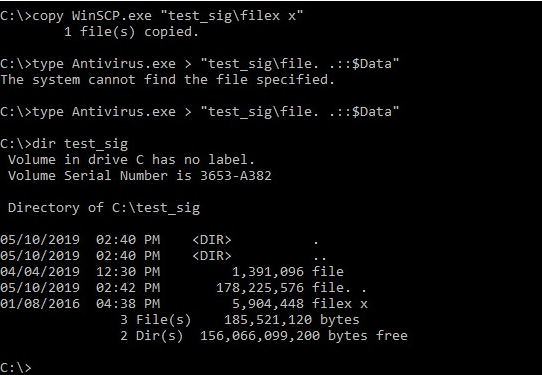
Here are the files we have created above:
- Microsoft’s taskmgr
- Fake malware with the name “file..” having an executed status
- The “filex x” that has the signature from WinSCP
We need to find a way of processing the “file..” binary. However, it is not an easy task because, by default, the Windows API automatically removes the “..” from the file name and starts the taskmgr, instead.
To handle this issue, let’s use the following code:
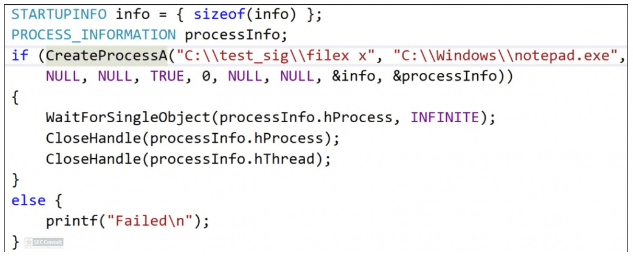
The code calls CreateProcessA, which invokes a process from “filex x” (in this case WinSCP). Once the code compiles, WinSCP starts.
Instead of doing the normal start, we’ll initiate it inside a debugger. Thereafter, we’ll set a breaking point at the function that makes it to call.
“bp ntdll!NtCreateUserProcess”.
With “g” (go) we can start our program in the debugger and hit the breakpoint. At the breakpoint, the current stack can be dumped (“dq rsp”).
We then dump the 12th pointer on the stack and leave the 4th one, as it is the pointer to the address of the filename. The filename at this point is normalized to start with \??\C:\…
The normalization stage removes the “..” from the filename, which explains why we have the C-code that does not use the “file..” as the process name.
However, the normalization that has taken place can have its values modified.
After that, let’s continue with the execution of “g” and see what happens. The “file..” (in this case, our Malware) is executed.
If you click on the process controlling the task manager and select “properties”, you’ll see a valid signature from Microsoft.
The file with “filex x” (the WinSCP), gets into the running process under the explorer because the path was set before NtCreateUserProcess was called.
If we use the Windows PowerShell, we can get the same output.
It can be a bad or a good thing, depending on what the attacker wants to accomplish.
The intention can be to start a process (introduce a Malware), rename or remove a file, or replace a valid file with the same name.
If any of these scenarios is implemented, the task manager will show the effects as the processing of the explorer requests is also taking place.
The notable thing is that this trick will happen at the same time as the process is launching.
The process illustrates the working of an installed endpoint protection system that checks for every launching process and confirms if the binary is known in the cloud.
The endpoint protection may use a wrong binary to verify if the hash is already known. The debugger is not needed for the creation of such processes.
An application can hook onto the NtCreateUserProcess function and implement the modifications.
Windows CMD Tricks
There is no relationship between the tricks we will share here and the file system tricks. You can write ^ at any location and the command will ignore the symbol.
For example, using “calc.exe” is similar to “ca^|c”; what matters is that the ^ is not the last symbol and that they are not used one after the other.
You can also use the double quotes without any restrictions as the quotes can be the last character or used several times.
For instance, to apply double quotes to invoke the calculator, use ^ca^”^”^|c^”.
The same reasoning can be used on zero-length environmental variables that are accessible via %name%. If the variable has a length of zero, “cal%name%c” would invoke the calculator.
All this is possible because the environmental variables have no default length of zero; so, it cannot be used directly.
However, you can call a substring on an environment variable with a special syntax (:~start,end).
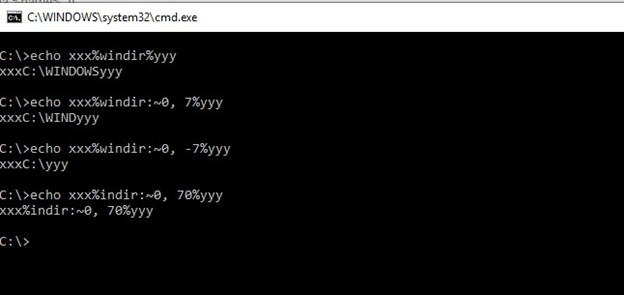
On Windows, the “/” is used to denote paths instead of the “\”. For example, C:\Windows /\/\sytem32\calc.exe is similar to C:\Windows\system32\calc.exe.
However, here’s how to access the binary through the UNC path and bypass the “C:\” pattern: \\127.0.0.1\C$\windows\system32\calc.exe.
You can use the same tricks to defeat blacklist approaches such as when the PowerShell is restricted, an attacker calls the power^shell.exe to bypass restrictions, or the calc is restricted.
You can try to execute the following command when facing any of the restriction scenarios:
^”%Localappdata:~-3%^%SystemRoot:~0,1%^”
The above commands will start the calculator. Similarly, you can use the same format to start other restricted programs or applications.
Protect yourself and discover all permissions owner on your Windows fileservers!
Pass your next security audit without worrying about security leaks!
Get your free trial of the easiest and fastest NTFS Permission Reporter now!




Leave a Reply
Want to join the discussion?Feel free to contribute!