How to Prevent Privilege Creep With FolderSecurityViewer
Ensuring the right access privileges are aligned with appropriate user roles is usually the headache of the IT department.
If there is a mismatch between a user’s responsibilities and their access privileges, it poses serious security risks, including data breach, exfiltration of sensitive information, and implantation of viruses and worms on the company’s systems.
In this article, we are going to talk about how to prevent privilege creep using a versatile tool known as FolderSecurityViewer.
What Is Privilege Creep?
Typically, privilege creep refers to the steady gathering of un-audited access rights beyond what a person requires to complete their tasks.
If a user requires rights to access an IT infrastructure, and sufficient justification has been given, those rights should be given.
However, when that same individual no longer needs those rights, and nothing is done to remove them, they remain unchanged. Over time, with the addition of more roles, a person can gather unnecessary and insecure rights.
How Privilege Creep Occurs
Simply, privilege creep takes place when users’ privileges are not cleaned out, especially after changing roles. Promoting employees, demoting employees, or carrying out transfers within departments are the major cause of access creep.
For example, a manager is hired and granted the access rights to the sensitive IT systems in a company. After some months in the position, he is demoted and a new manager is hired to replace him. However, instead of the access rights of the old manager being revoked, he still retains them.
The same scenario can happen when an employee is transferred to another department or an employee is promoted to a higher position. Also, if an employee is granted temporary access permissions to cover for vacations or prolonged absences, and the rights are not rescinded, privilege creep can ensue.
Dangers of Privilege Creep
Privilege creep usually leads to a two-fold security risk to organizations. The first risk occurs when an employee who still has uncleaned privileges gets tempted to gain unauthorized access to a sensitive system.
In most organizations, security incidences take place because of dissatisfied employees attempting to cause damage or just ‘make a point’. If such employees have unnecessary privileges, they can maliciously gain entry into systems away from their immediate work station, making finding them out difficult.
Second, if the user account of an employee with excess privileges is hacked, a criminal can collect more information than if the privileges of the account were not excessive. If an account is compromised, it becomes the property of the attacker, and it is more lucrative if it has excess rights.
How to Avoid Privilege Creep
Carry out access reviews
The best technique of avoiding privilege creep is carrying out frequent, thorough access reviews. The IT department should regularly confirm every employee’s access rights to ensure the unnecessary accumulated privileges are revoked.
If a company has invested in a robust identity and access management system (IAM), undertaking access reviews become less taxing and making decisions concerning employees’ continued access become easier. Implementing an IAM system will ensure granted access privileges are appropriately authenticated and audited.
Importantly, when conducting access reviews, the principle of least privilege should be applied. The permissions granted to users should be limited to the minimal level that enables them to carry out their tasks without any difficulties. For instance, someone in the HR department should not be given the privileges of accessing the organization’s customer database.
Access reviews should be maintained throughout the year, with a frequent rotation in every department within the company. Every employee, from the CEO to the lowest-ranked, should have their access permissions periodically reviewed, especially when there is a change in roles.
Communication of changes in roles
In case any employee changes roles, it should be promptly communicated to the IT department. If formal notification is not done, the IT department may not revoke the employee’s access rights, which can lead to harmful consequences.
So, the HR department should work together with the IT department to avoid such lapses, and enhance the security of the company’s infrastructure.
Ensure privileges are aligned
By ensuring the privileges of each employee are aligned to their specific roles and responsibilities, it becomes easier to prevent this creeping monster.
In the company’s employee lifecycle management policy, a comprehensive documented process should be included that clearly outlines the IT-related actions.
In case of any changes to roles, prompt notification should be made to the IT department for updating of the privileges and closure of redundant accounts.
How FolderSecurityViewer Can Help
The task of preventing privilege creep is delicate and demanding. If you try to manually sieve a big number of users’ privileges, it can consume a lot of your time and drain a lot of resources, besides the mistakes and oversights that can ensue.
Therefore, investing in an IAM system can greatly reduce the extensive costs of tackling the security vulnerabilities ensuing from privilege creep as well as misaligned or abused privileges.
For example, the FolderSecurityViewer is a powerful free tool you can use to see all the permissions accorded to users. After analyzing the permissions, you can clean them out, and reduce chances of privilege creep occurring.
First, you’ll need to download the tool from here.
After launching the tool, you’ll need to select the folder you need to review its permissions, and click the entry Permissions Report of the context menu for the magic to start.
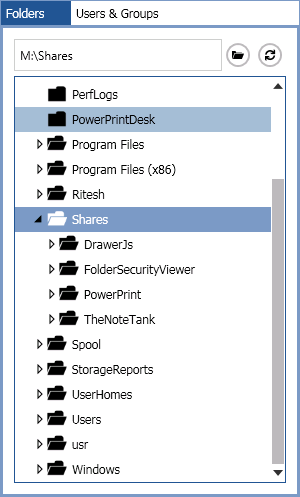
You’ll then be provided with a comprehensive permissions report containing several things, including the names of users, department of users, and their respective allowed permissions.
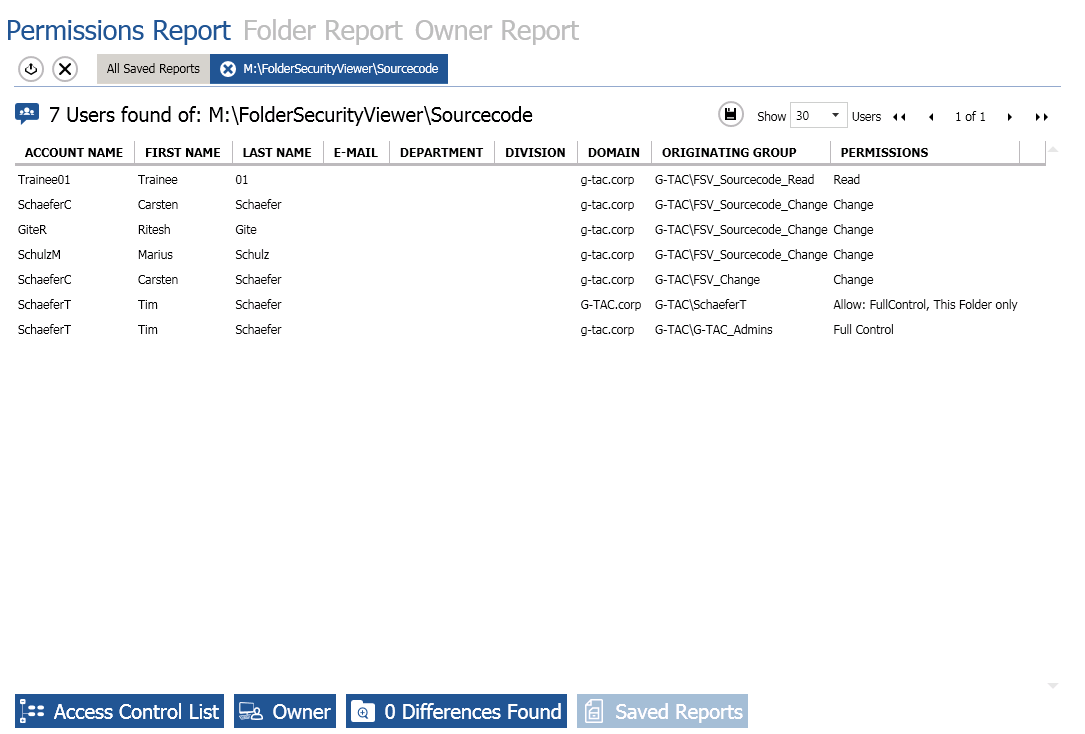
If you want to get more information, you can click on the “Access Control List” button and see the various privilege rights accorded to users.
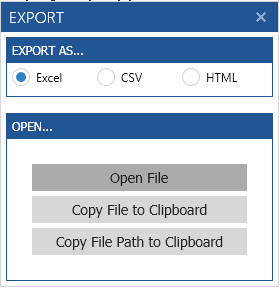
You can also export the permissions report in Excel, CSV, or HTML format, and make more analysis.
After carrying out the access reviews using FolderSecurityViewer, you can audit identities and permissions to ensure role-based privileges are applied and excessive privileges are revoked.
Conclusion
The FolderSecurityViewer is a wonderful tool you can use to provide you with visibility into the permissions and access rights for your IT infrastructure. This way, you can easily prevent privilege creep and avert costly security breaches from occurring.




Leave a Reply
Want to join the discussion?Feel free to contribute!