Managing Data Access on Windows Fileservers: Processes and Responsibilities
Step 2: Processes and Responsibilities
Definition of Business Processes and Responsibilities
The second step in properly managing data access on Windows fileservers is to clearly define business processes and responsibilities.
Each user has a specific responsibility within the business premise. To carry out the various processes and realise the business’ goals, every user should be granted the privileges to access certain resources and undertake particular tasks.
However, allowing users uncensored access to system and network resources within the organisation can weaken its security and stability.
Importantly, access to computer or network access should be restricted based on the responsibilities of individual users within the organisation.
If a user is not responsible for a particular business process, there is no need of granting him or her permissions to perform the task.
Since controlling access to business data is the foundation of data security and, in some cases, of data privacy, universally applicable, mandatory processes must be defined together with someone from senior management.
The process of defining processes and responsibilities should be based on a comprehensive assessment of how a business operates, and should include input from the management.
The management must also be willing to give its full support to the implementation and enforcement of the role-based access control (RBAC) rules.
What are Business Processes?
Business processes define work flows and responsibilities. In addition, processes can also outline the tools required or recommended for the execution of said processes.
Some examples of processes:
- Data requests
- Requesting permissions
- Changing permissions
- Withdrawing permissions
- Creating new objects
- Assignment of and changes to responsibilities
- Assignment and modification of owners
- Expansion of storage requirements
Processes are often presented in the form of diagrams. Below, you will find a simple example of an assignment of permissions.
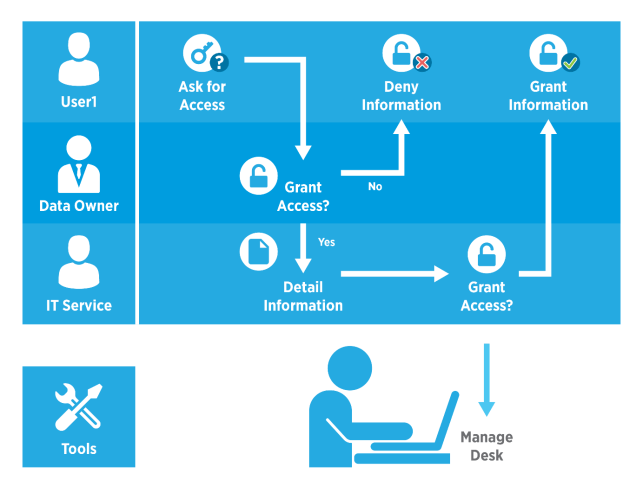
Compliance with these processes must be mandatory.
To ensure mandatory compliance, one must have the support of senior management or IT management, who must then communicate the necessary access control rules to all employees.
What are Responsibilities?
Responsibilities are defined based on the user’s competency, functions, and authority.
In an organisation, responsibilities can be created, changed, or discontinued depending on the prevailing needs and goals to be accomplished.
Responsibilities describe the types of processes that users are allowed to accomplish within the organisation.
Through assigning responsibilities to users, the management can ensure various processes are completed based on the intended goals to be achieved.
The IT department should work together with the management to ensure that users do not have access to resources beyond their stipulated responsibilities or level of control.
In case of changes in responsibility, the access level for that user should be adjusted as soon as possible. If a user has unnecessary access to a particular system, it can hamper the smooth running of the business process.
The following scenario illustrates how responsibility can be managed:
Irene works in the Marketing department and requires to view—but not create or modify—certain files from the Finance department. The Finance department, which is fully responsible for these files, utilises access control to restrict the users allowed to have Read-only, Write, or Modify access to them.
Irene is granted Read-only permissions to the Finance files. Likewise, the IT department resolves that preventing users such as Irene from creating changes to their systems can assist processes within the company run smoothly and enhance security.
Consequently, IT moves Irene and other users to the Users group, which restricts their actions to their assigned responsibilities and prevents them from making any reconfigurations to the system.
As a result, Irene has access to the resources she needs to undertake her responsibilities, the security of the processes within the organisation are improved, and stability of the network is solidified.
Responsibility of the Executive Board or Management
Administrators are responsible for the management of IT infrastructure, but they are not responsible for file structures or business processes concerning the assignment of permissions to data or other IT objects.

Often there will be few or no documented IT processes, which indicates that documentation is not being done well enough.
Unfortunately, senior management will often place the responsibility for permissions in the hands of the IT administrator.
This is not a good idea. For instance, decisions regarding whether an employee shall have access to sales data will time and again prove to be poor decisions, especially if the “applicant” has better argumentation skills than the IT staff member or is located in another level of the company hierarchy.
In other words, if the head of the “service” department wants his employees to receive permission to access data in the “sales” department, the decision should only be made by the head of the “sales” department.
Managing Changes in Responsibilities
The responsibilities of users should be aligned with their data access privileges. In case of changes in responsibilities, the previously allowed rights should be revoked and proper adjustments made.
For example, giving new staff members with new responsibilities a handbook that describes the IT environment of the company and all of the company’s IT processes has been proved to be extremely beneficial in managing changes in organisations.
If a new employee requests for access rights, the data access privileges should only be awarded when the mandatory approval process has been successfully carried out – without exception.
To demonstrate the execution of the individual steps in a process, it is necessary to have so-called “Use Cases”. Use Cases are step-by-step explanations of how an administrator (for example) creates a new file folder with individual permissions, especially when users change roles in an organisation.
Further examples are:
- Awarding a new user permission to access a particular data area
- Revocation of an old user’s permission to access a particular data area

Lack of Compliance with Business Processes and Requirements
Employees will frequently attempt to circumvent business processes. A typical example of this would be a call to the IT department, without filling out the required permission forms, to gain certain permissions.
This will typically be justified by arguments like “it’s important”, “it’s urgent”, “I forgot to fill out the forms, but the new staff member is already here”, “I have specific instructions from the boss”, “if I don’t get the permissions immediately, then….”
In such cases, the IT staff member will normally fail to document the assignment of permissions.
The reason that there was “not enough time” will often be used to circumvent clear instructions regarding file folder structures or permission concepts.
The following scenario is a good illustration of this:
There is a requirement that access permissions for a file server may only be given on the file folder level. Despite this, the department head makes a request to receive the necessary permissions to access a specific file.
To resolve this conflict, the IT administrator will have to create a new file folder and put the file into it. It would then be necessary to create and assign all permissions for this file folder.
Instead of doing that, IT administrators will frequently try to save time and give the department head the requisite permissions for the file as a “one-off” exception.
Best Practices
Here are some practices you should follow to ensure proper management of processes and responsibilities:
- Implement the principle of least privilege, where users are granted the minimum access rights to carry out their responsibilities. This assists to ensure that if a user’s account is hacked, the consequences to the business processes are minimized by the limited rights the user possesses.
- Periodically audit the responsibilities within the organisation to ensure they are aligned with the stipulated processes. If not, revoke the unnecessary permissions and make proper adjustments.
- Do not give in to the temptation of creating exceptions for circumventing the already assigned responsibilities and rules. If you do this, you will be avoiding complying with business processes and requirements, and endangering the security of the organisation.
- Recognise that not every employee requires a starring role, and properly grant access rights based on the stipulated responsibilities, and nothing more.
- Ensure that the IT department works together with the senior management so that employees’ access privileges are properly aligned with their responsibilities within the organisation.
Download Checklist
Click here to download a checklist that will assist you with defining business processes and responsibilities.
Next…
In the next step, we’ll talk about using security groups for assigning permissions.



Leave a Reply
Want to join the discussion?Feel free to contribute!