NTFS Allow and Deny Permissions
NTFS (New Technology File System) permissions provide an essential way of maintaining a good level of control to your critical IT infrastructure.
These permissions are normally granted to groups as a way of determining the users able to access the files and folders.
Understanding NTFS Allow and Deny Permissions
When assigning permissions, you will need to specify whether a group or an individual user has access (Allow) or do not have access (not Allow) to the system.
Even though it’s recommended to use the Deny permission sparingly because it can enhance the complexity of administration, there are some situations where its use is necessary and more beneficial.
For example, you can apply explicit Deny permissions to a specific user only when it is essential to overrule the permissions that are otherwise granted for the group to which the user has been added.
In this article, we are going to talk about how to comfortably combine NTFS Allow and Deny permissions.
Permissions Precedence
When different permissions settings have been applied on an object, the system usually tries to resolve the various permissions to establish which ones should take precedence.
Here are some guidelines for solving permissions precedence issues:
1. The “Deny” permissions usually override “Allow” permissions (in most cases).
For example, let’s say that you have a user called Agnes, and in this case explicit permissions have been applied. The first permission is a Deny permission that denies Agnes from accessing the object. And, the second permission allows Everyone to enjoy access.
When permissions are applied to files or folders, the Deny permission will always take precedence. As such, if the system checks the permission list from top to bottom, it first notices that Agnes has been denied, and will not grant her access.
2. Explicit permissions usually override inherited permissions.
Explicit or direct permissions refer to those permissions that are applied automatically after the object is made while inherited or indirect permissions refer to those permissions that are extended to an object for being a child of a parent object.
When explicit permissions and inherited permissions are combined together, the former usually takes precedence.
Let’s say that this time Agnes has been allowed access. Next, inherited permissions have been set to Deny Everyone access. In this case, will Agnes still have access?
Of course, yes.
Even though there is a Deny permission, Agnes will still be given access. Why does it happen this way?
Deny permissions are usually sorted towards the top of the NTFS permissions list. However, explicit permissions are predominant.
In this example, since Agnes has been granted explicit permissions that allow access and inherited permissions that deny access, she will still enjoy access. This is because explicit permissions usually take precedence over the rest.
Also, it’s important to note that if the explicit permissions allow access, then the inherited permissions will never be checked.
As such, if the inherited permissions have Deny permissions applied, and explicit permissions have Allow permissions applied, then the inherited permissions will never be checked, making the Deny permissions irrelevant.
Here is an example that demonstrates how an explicit allow permission will take precedence over an inherited deny permission.
- On the Windows explorer, right click on the folder named “Agnes” and select the “Properties” option. (Note that the folder has a subfolder named “Templates”).
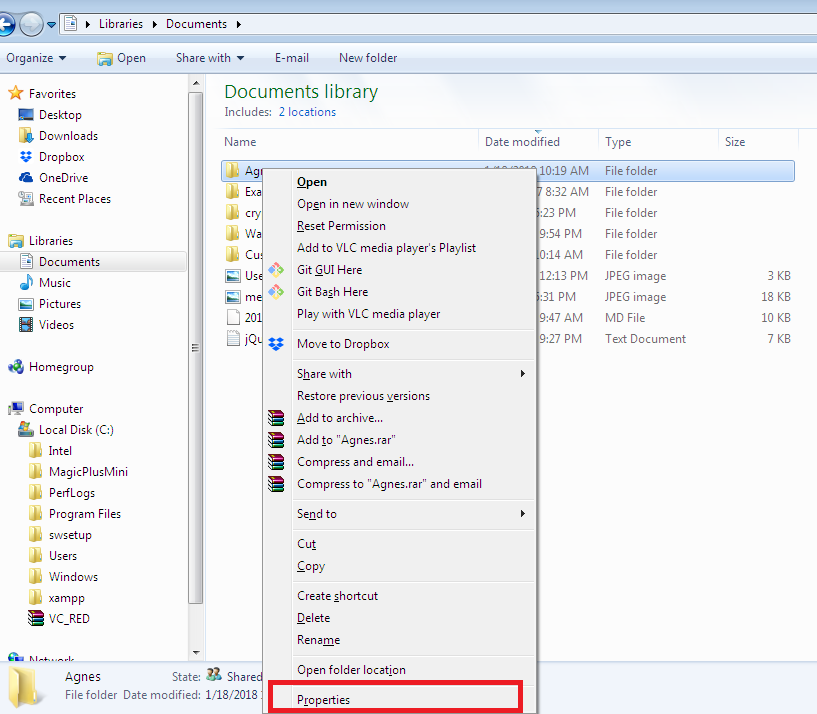
- On the properties window, select the “Security” tab.
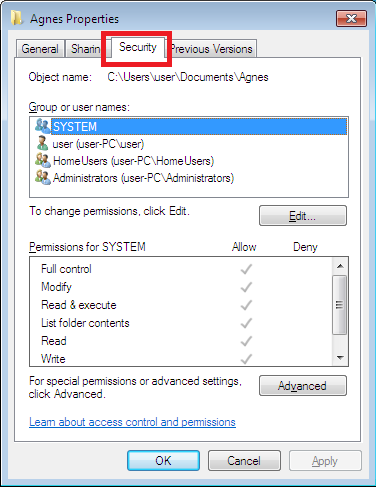
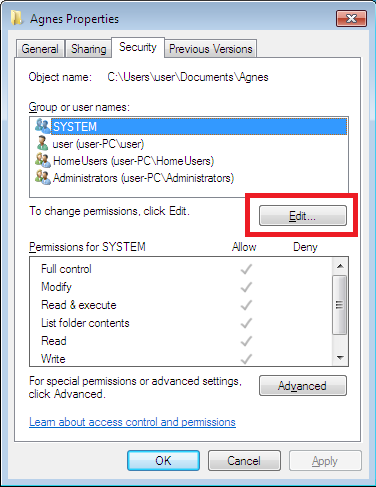
- To change permissions, click on the “Edit” button and then press the “Add” button.
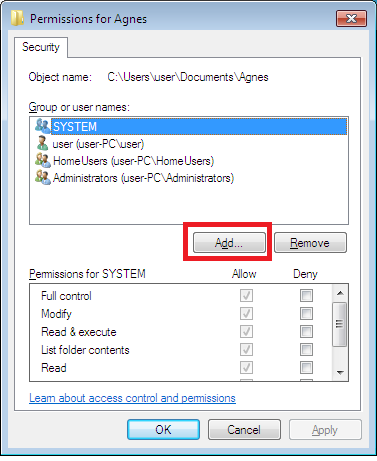
- On the window that pops up, add “Everyone” to the list of permissions.
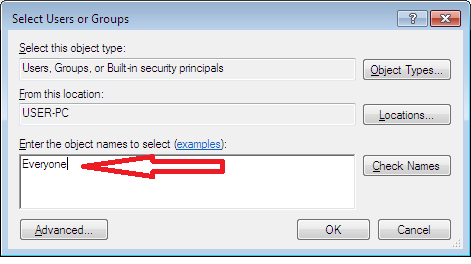
Once Everyone has been added to the list of permissions, everyone will be granted other permissions, including “Read & execute” permissions—this takes place by default.
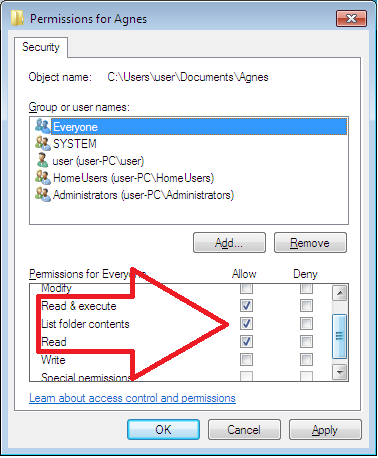
- Consequently, to prevent all users from writing to the folder, uncheck the default Allow permissions and click the Deny permissions for “Write”.
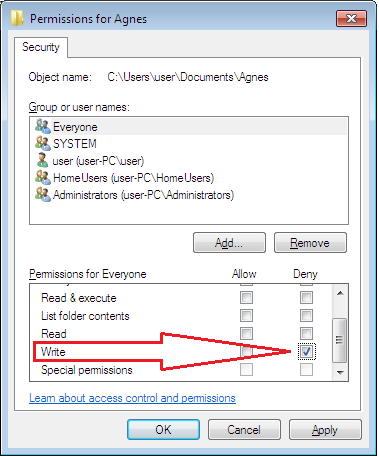
If you press the “Apply” button, a warning dialog box will appear stating that Deny permissions will take precedence over other permissions.
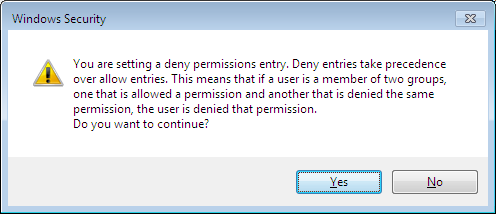
Click “Yes” to continue.
- After the permissions have been set, if you try to create a new file or folder in the folder or its subfolder, you will see an error message, indicating that access has been denied.
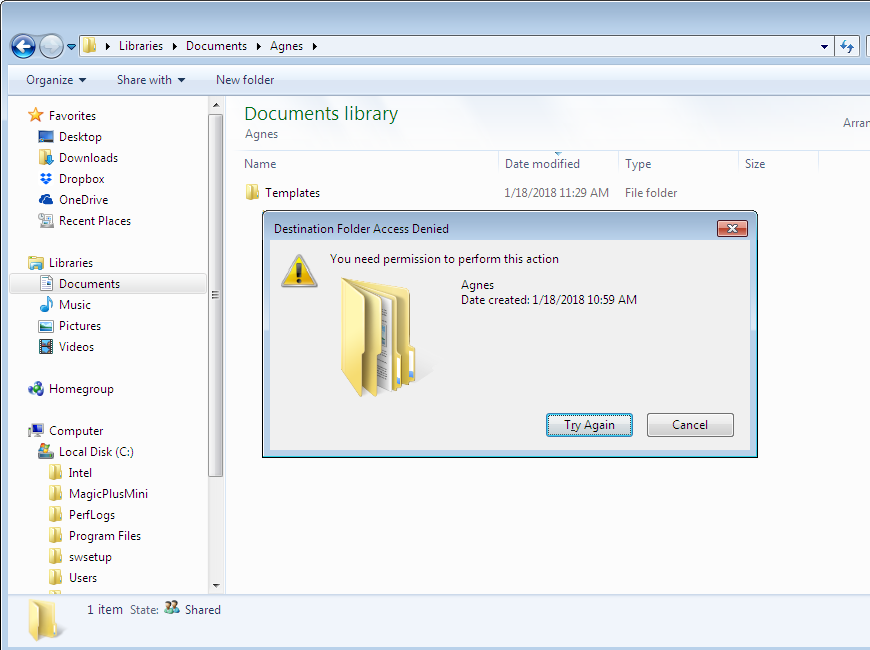
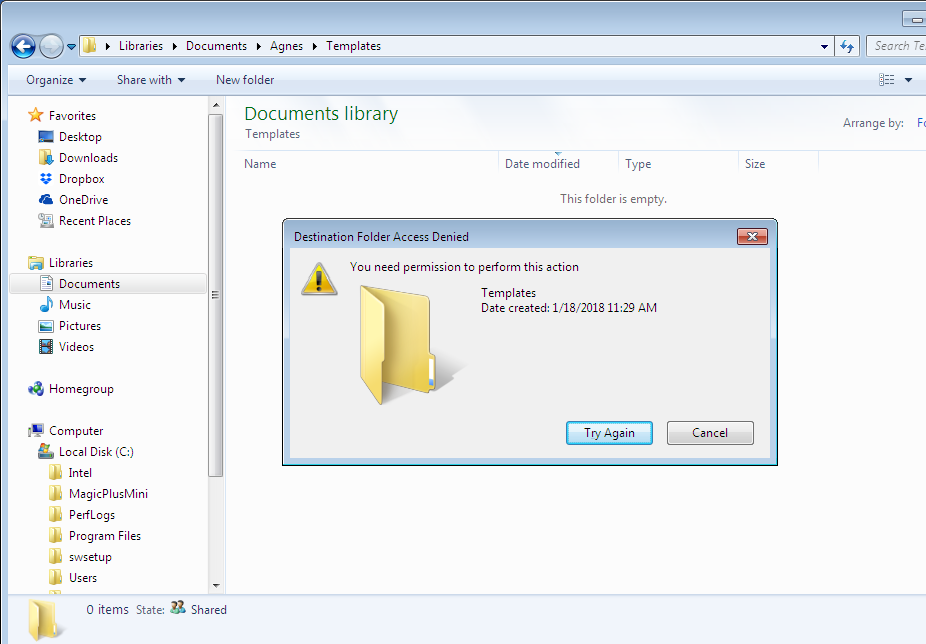
- The next step is to right click on the “Templates” subfolder and select the “Properties” option.
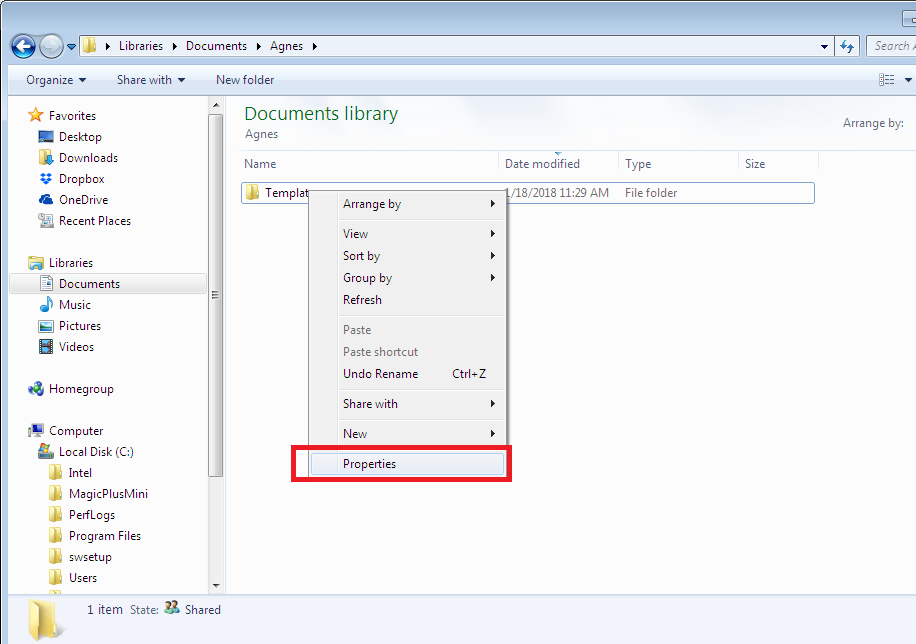
- On the subfolder’s properties, select the “Security” tab.
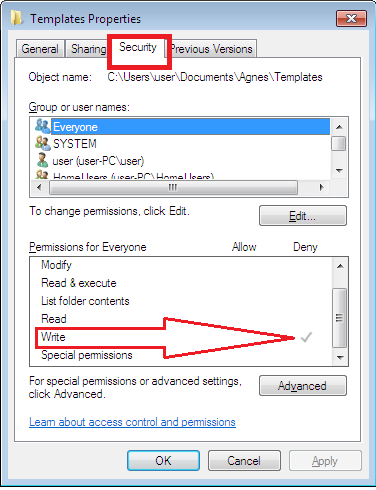
In the permissions list, notice that “Everyone” is present and the Deny permission for “Write” is inherited.
- For example, if you want to add explicit “Write” permissions to HomeUsers, click the “Edit” button.
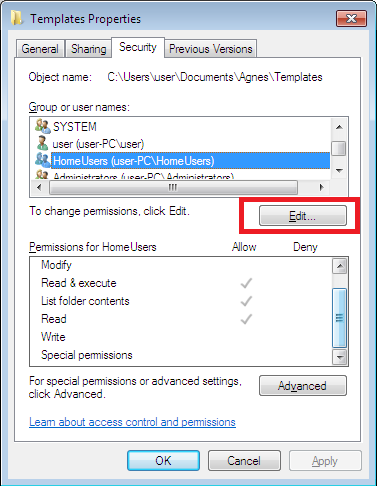
Then, on the Window that pops up, click the Allow “Write” permissions, and apply the settings.
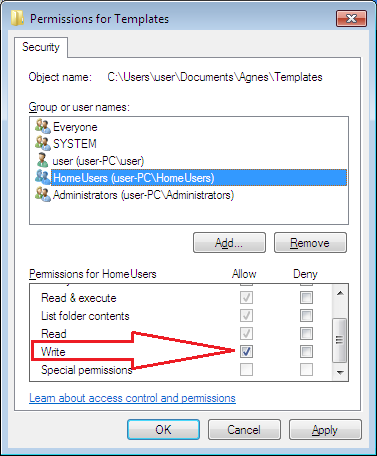
Therefore, the subfolder will have Everyone Deny Write permissions that are due to inheritance and the HomeUsers will have Allow Write permissions that are explicit.
- With these permissions set, you will now be able to create files and folders in the subfolder but not in the parent folder, as shown below.
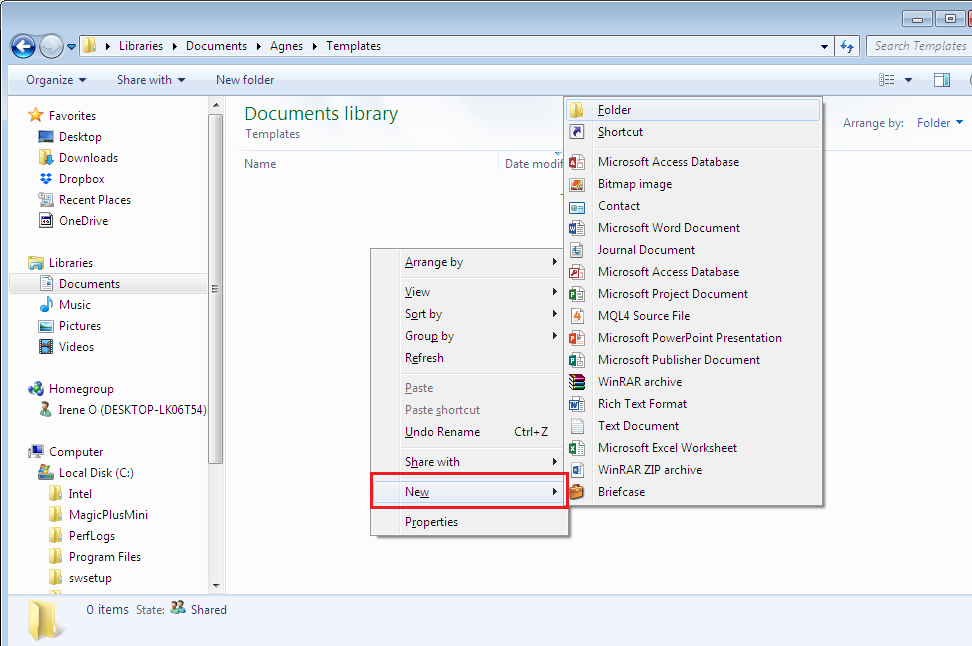
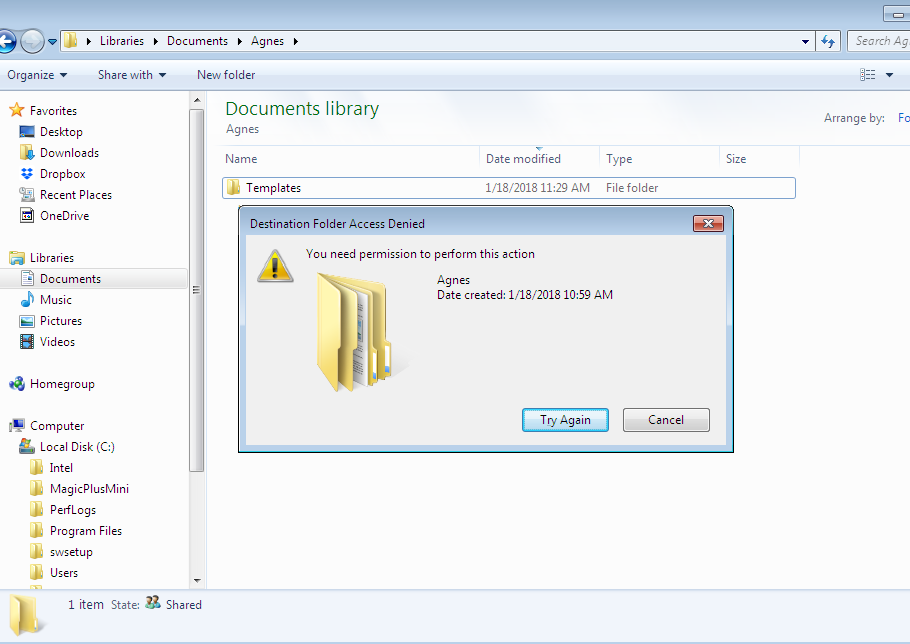
3. Access permissions that are inherited from neighboring relatives override those inherited from faraway predecessors.
For example, if access permissions have been propagated from the object’s parent folder, then they will be prioritised above those rights propagated from the object’s grandparent’s folder, and to others.
4. Permissions privileges from multiple same-level user groups are cumulative.
If user groups are created at the same level–relating to having the same explicit or inherited permissions or Deny or Allow permissions—then the permissions can be aggregated.
Let say that Agnes belongs to two security groups. One of the groups has given her the Allow permission of “Read” while the second one has given her the Allow permission of “Write”.
Consequently, she will enjoy read as well as write privileges, if the other guidelines above are also taken into consideration.
However, if the user groups are not at the same level, the permissions can cause unnecessary problems, especially if Deny permissions are used.
For example, if Agnes belongs to two security groups: group A and group B. If there is a file share, and members of group A are denied access (Deny permissions applied) while members of group B are allowed access (Allow permissions applied), it can lead to problems.
Since Agnes belongs to both groups, she will now be denied access to the file share, which may not be the required result.
So, how do you deny access to group A members while still allowing access to users belonging to both groups?
The simple solution is to remove group A from the access control list. It ensures they do not access the file share because they lack the required privileges. This way, it will allow only group B members to be granted access.
As a result, users belonging only to group A will be denied access to the file share. And, users belonging to both groups, like Agnes, will be granted access.
Because of such reasons and complexities, most administrators will only apply Deny permissions if there are no other means of achieving the intended objectives.
Conclusion
As you can see, most of the results accomplished using Deny permissions can be conveniently achieved using Allow permissions. Therefore, most administrators try avoiding using Deny permissions—although sometimes it is unavoidable.
In summary, if you have to use Deny permissions, ensure you keep to the following hierarchy of permissions precedence.
(Note that the list starts from the permissions with the highest precedence to permissions with the lowest precedence).
- Explicit Deny
- Explicit Allow
- Inherited Deny
- Inherited Allow
Useful Resources
Check out our posts about similar topics:
- https://blog.foldersecurityviewer.com/understanding-ntfs-permissions/
- https://blog.foldersecurityviewer.com/ntfs-permissions-vs-share-permissions/
- https://blog.foldersecurityviewer.com/best-practice-ntfs-share-permissions/
Do you have unclear NTFS Permissions assignments?
Do you have too many special permissions set on your fileservers?
Or blocked NTFS Permission Inheritance?
Protect yourself and your clients against security leaks and get your free edition of the easiest and fastest NTFS Permission Reporter now!




Leave a Reply
Want to join the discussion?Feel free to contribute!